 Hello Friends!
Hello Friends!
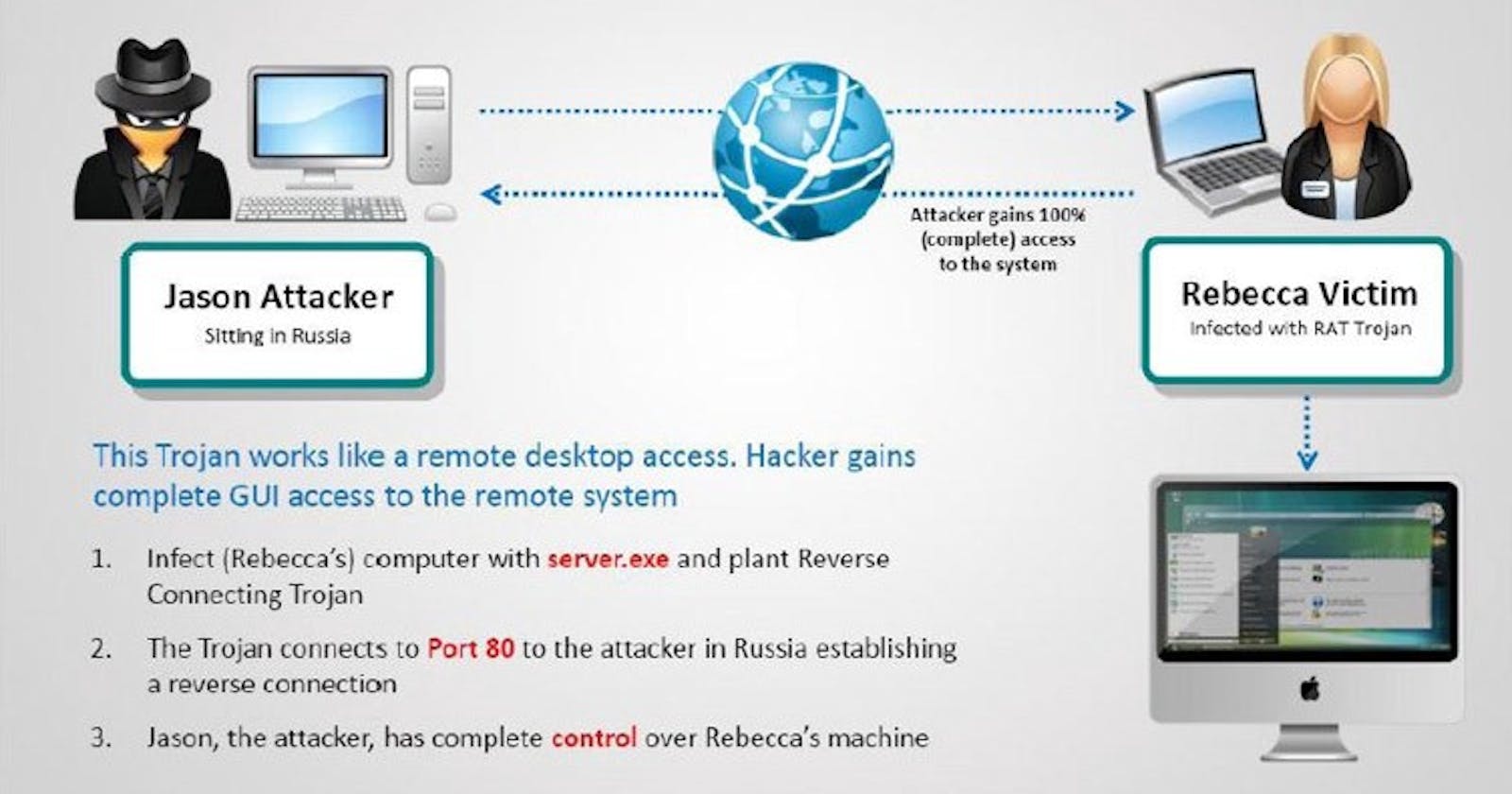
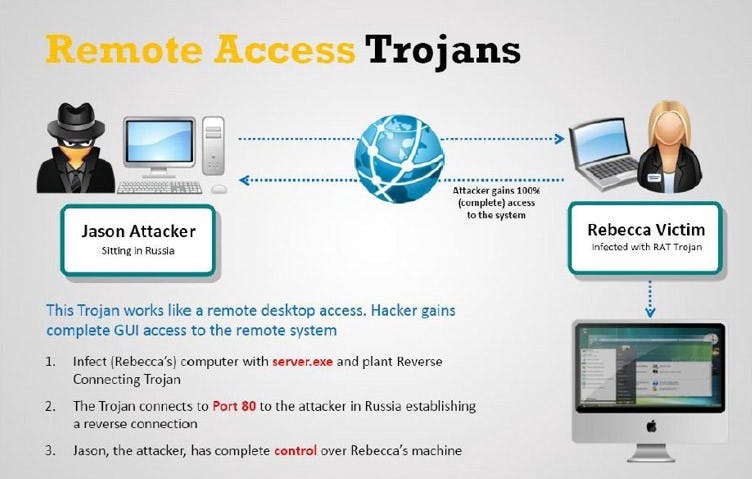
Today I want to tell you about a type of cyber attack called Remote access Trojan (RAT) this type of attack occurs when an attacker gains complete access to your computer for malicious activities. it gives the hacker to explore your files, watch your screen and harvest your login credentials.
A hacker can gain such access by allowing you to download files or emails from untrusted sources such as websites and blogs or software into your computer. Basically, RAT infects your computer to give the attacker unlimited access to the data on your computer.
Different RATs exist for different kinds of attacks, some hackers even develop their own or modify an existing one to meet their desired purpose of attack which is to gain administrative access to your computer.
BACK ORIFICE: This type of RAT has been around for a long with its origin in the USA. It attacked windows and can hide within a specific operating system
ZEROACCESS: This one is used to steal banking and financial information. It is difficult to identify due to its highly advanced rootkit
BEAST: This is similar to the back orifice RAT with the same technology of getting the malware installed secretively on the victim's computer. it was developed in 2002 and attacks Microsoft windows from windows 95 to windows 10
MIRAGE: This type of RAT is mostly used by a group of Chinese hackers called APT15 to attack UK government contractors
The basic difference among these various RATs is that they are designed to carry out various attacks on systems using different methods to achieve an individual goal of the hacker.
How to protect yourself against Remote Access Trojans and other malware
- Always ensure that your security software and operating are up to date
- Regularly Bacup your data
- cover your webcam when not in use
- Do not click links or emails within unexpected sources
- Only download apps and software from sources you can trust